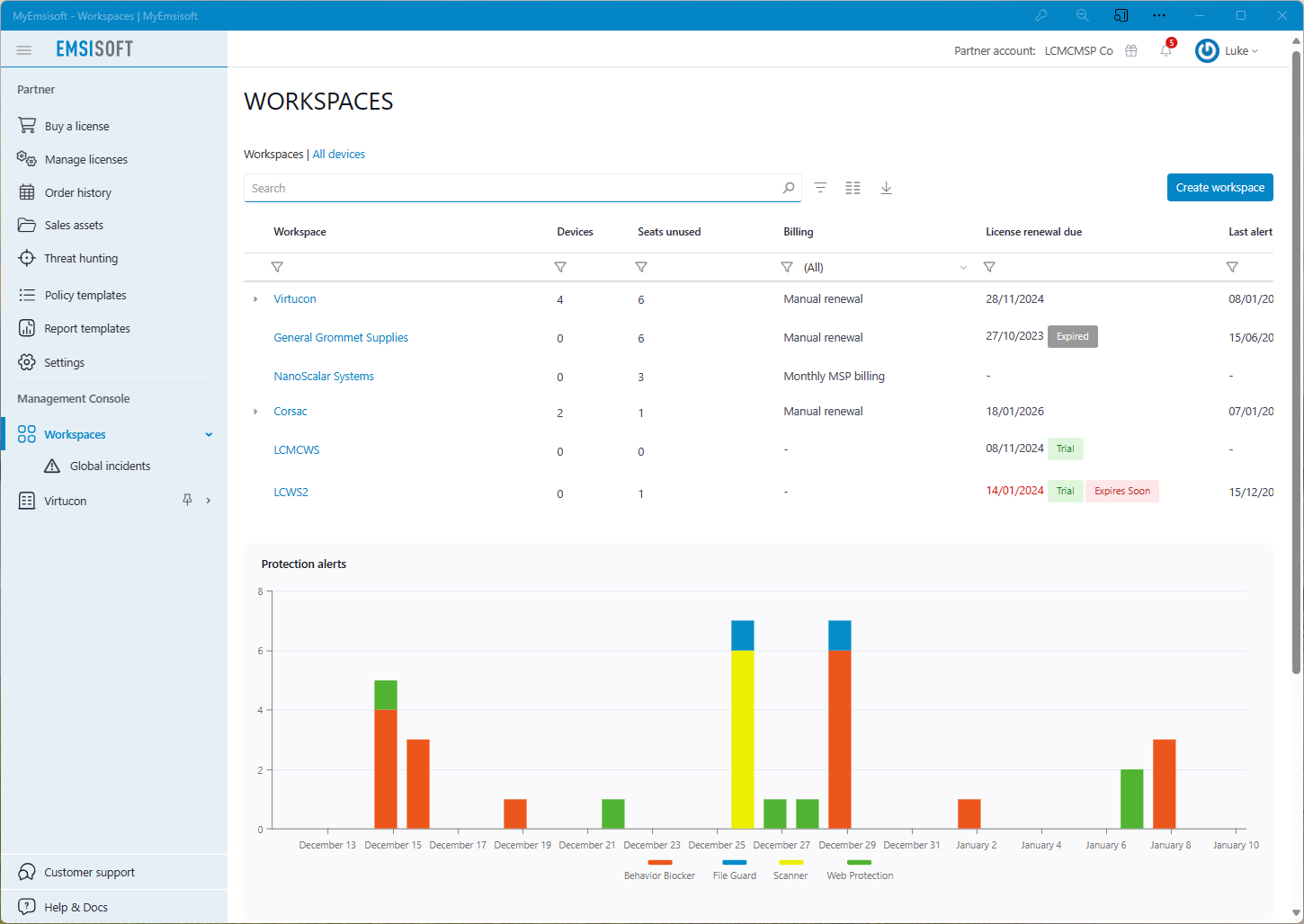
Malware spreads while security teams hurry to understand what happened and how
Get deep threat insights instantly.

Get deep threat insights instantly.
Suitable for organizations of all sizes and skill levels.
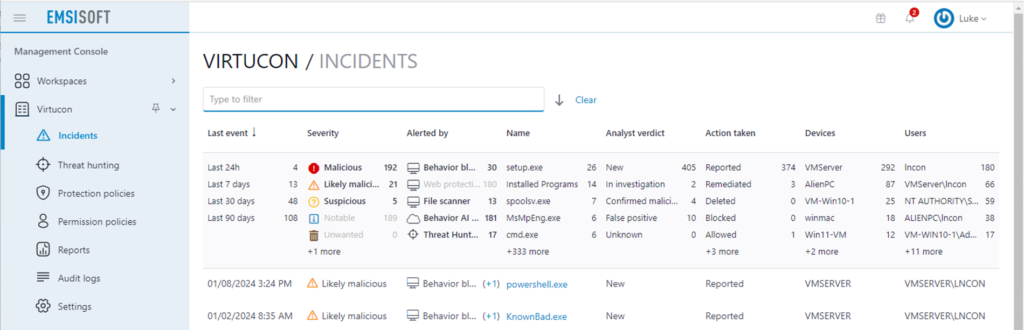
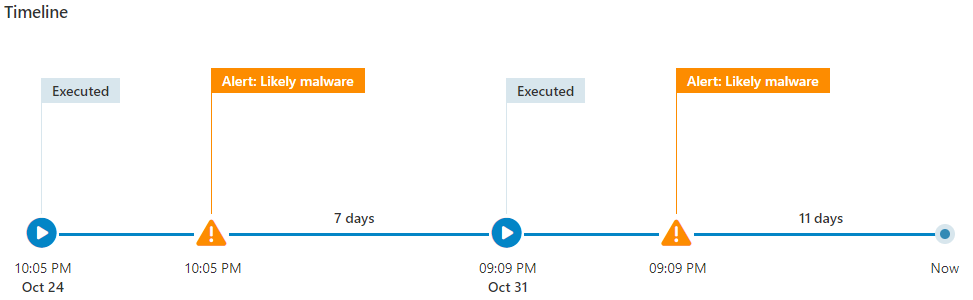
Quickly find out what happened.
Find out exactly where malware struck, how it happened, and prevent it from happening again.
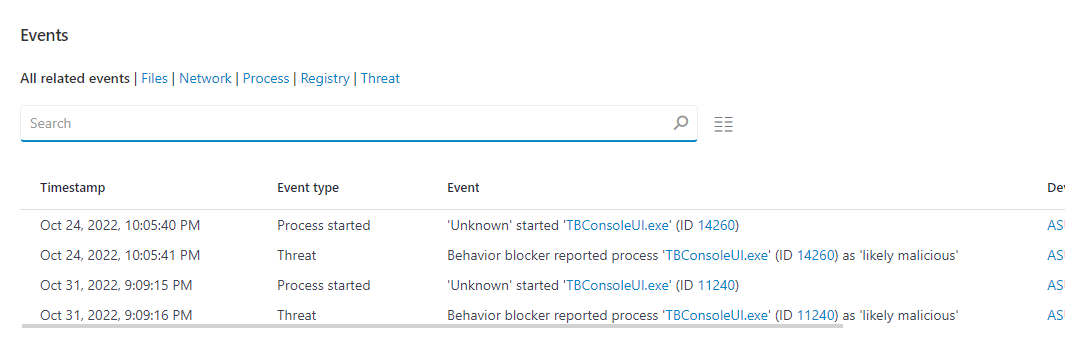
Combine application observation with behavioral analytics to determine if an application is malicious.
Classify unknown applications by observing application behavior and network traffic, gathering OS environmental data, and parsing extended local log data.
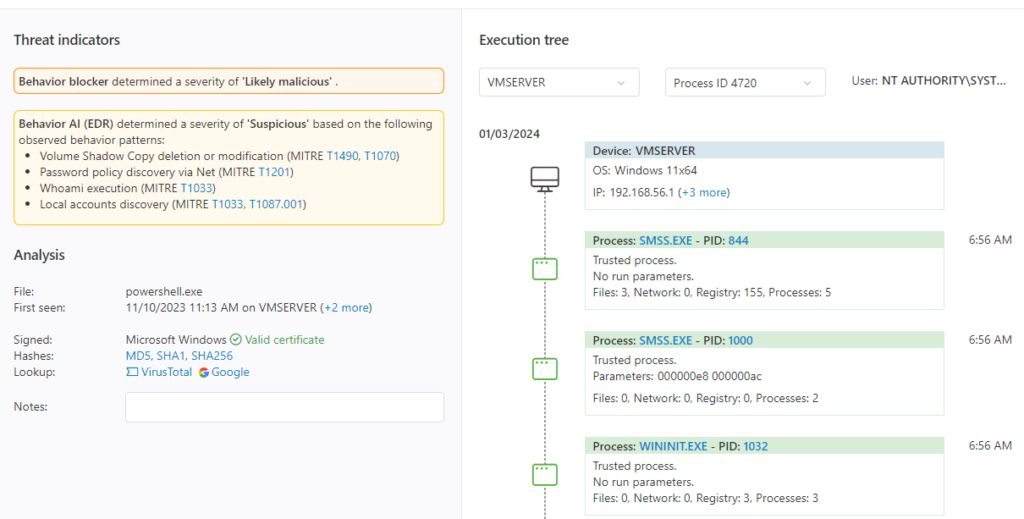
Analyze unknown application behavior using cloud-based behavioral analytics that take into account application behavior across all systems and compare application behavior against the MITRE ATT&CK framework.
Confidently filter real alerts from noise based on behavior scoring applications against 1000+ different known adversary tactics and techniques.
Find emerging threats quickly and easily.
Osquery is a powerful tool that gives you the power to look for indicators of compromise across every device under management instantly. Osquery lets you obtain information about operating system environmental variables, firewall settings, DNS cache entries, browser plug-ins, and much more.
Whether you’re looking for evidence of emerging threats like fileless malware, or just checking to see which systems have vulnerable applications or drivers, the Threat Hunting panel provides real-time information across all devices under management.
Select from a pre-defined list of common queries or write your own. A Linux Foundation Project, osquery has proven itself to be a time saver for security, compliance, and devops teams around the world.
Schedule queries and set alerts. Check for environmental variables out of bounds, or create queries that check script repositories, configuration files, and other critical data for changes. You know your network best!
Easily integrate Emsisoft EDR into your existing workflow.