WikiLeaks exposed how much governments spend on FinFisher malware to spy on their citizens

Surveillance technology provides “digital weapons” that governments use to combat cyber-crime. On the flipside, this kind of control is used by suppressive regimes against human rights defenders and other “selected” enemies such as critical journalists, members of different political parties or religious groups.
We wrote about this in July and asked “Is malware still malware if it’s used by legal authorities to track down criminals?” In 2011, we also made a brief statement about how and why our software detects “federal trojans”.
FinFisher surveillance software for government agencies is spyware that allows complete access to a target’s computer.
“This software is designed to be covertly installed on a Windows computer and silently intercept files and communications, such as Skype calls, emails, video and audio through the webcam and microphone.” WikiLeaks
[youtube http://www.youtube.com/watch?v=qc8i7C659FU]
A license contract for FinFisher’s software worth €287,000 was first found in the offices of Egypt’s secret police after the overthrow of its president in 2011, and more research by organizations such as Citizen Lab has revealed that it was also sold to suppressive regimes that spy on their citizens and that are known for their human rights violations.
Reporters Without Borders called FinFisher’s parent company, Gamma International, a digital era mercenary and one of the “Top 5 Enemies of the Internet” in its report on the organization, along with Trovicor, Amesys, Hacking Team and Blue Coat.
“They all sell products that are liable to be used by governments to violate human rights and freedom of information. […] Their products have been or are being used to commit violations of human rights and freedom of information. If these companies decided to sell to authoritarian regimes, they must have known that their products could be used to spy on journalists, dissidents and netizens. If their digital surveillance products were sold to an authoritarian regime by an intermediary without their knowledge, their failure to keep track of the exports of their own software means they did not care if their technology was misused and did not care about the vulnerability of those who defend human rights.” Reporters Without Borders
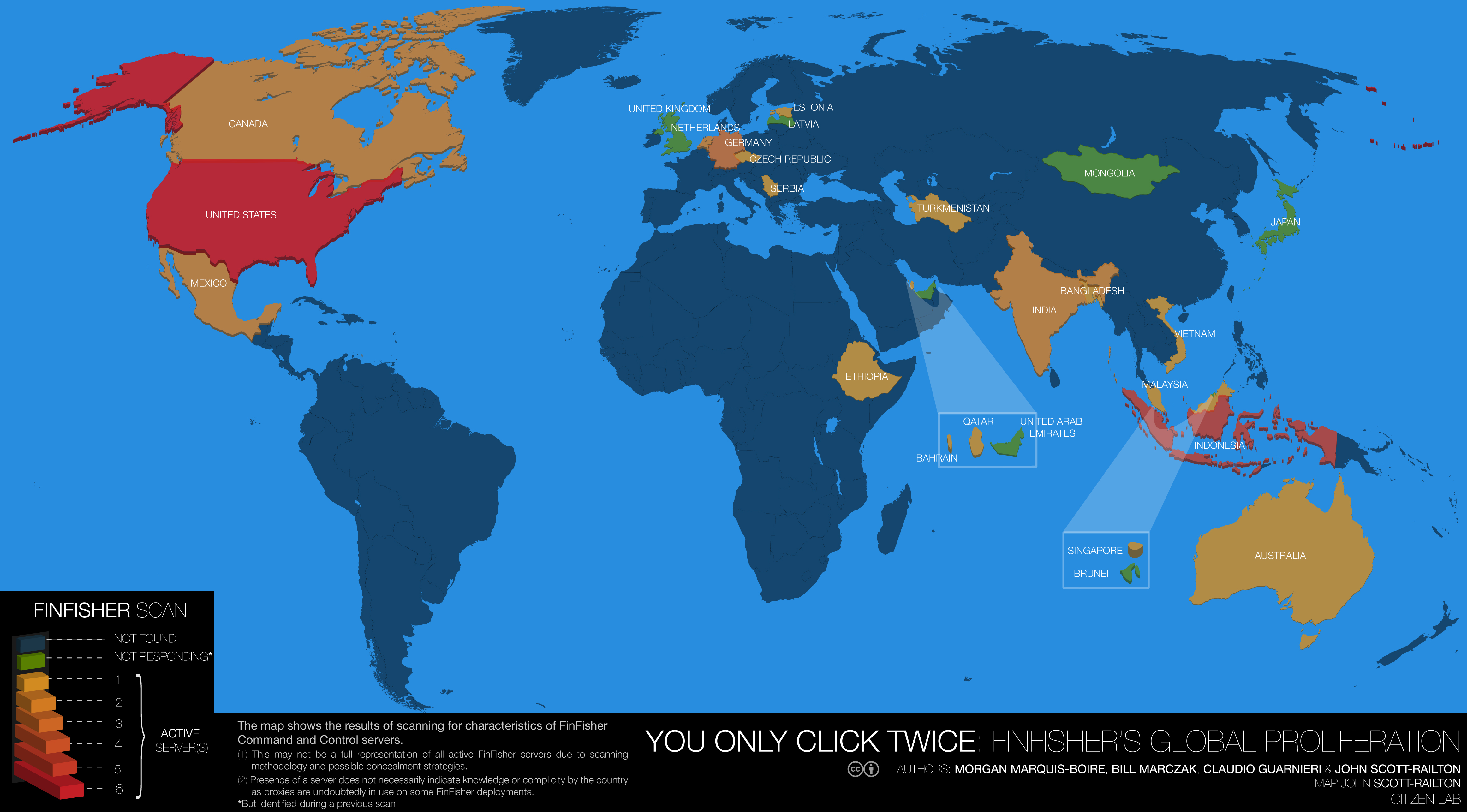
Map of global FinFisher proliferation. Source: Citizen Lab
In its latest release of information on FinFisher, WikiLeaks exposed a more detailed “customer list” of countries that bought licenses and how much they spent for it.
RELEASE: WikiLeaks Spyfiles4: surveillance weaponized German malware https://t.co/Jup9X5VSxY
— WikiLeaks (@wikileaks) September 15, 2014
How much each country paid for #FinFisher spyware. Click on the country and customer ID to see full billing data https://t.co/o1yWCx081n
— WikiLeaks (@wikileaks) September 15, 2014
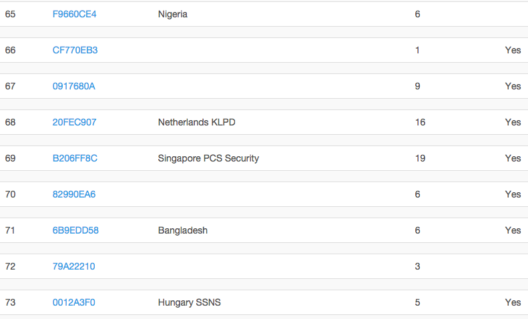
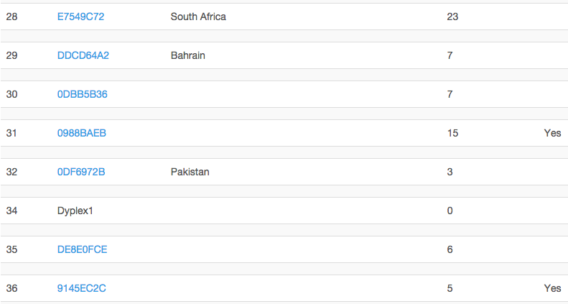
“Some customers were identified through the analysis of support requests and attached documents they provided to FinFisher support. This included Slovakia, Mongolia, Qatar State Security, South Africa, Bahrain, Pakistan, Estonia, Vietnam, Australia NSW Police, Belgium, Nigeria, Netherlands KLPD, PCS Security in Singapore, Bangladesh, Secret Services of Hungary, Italy and Bosnia & Herzegovina Intelligence.
Provided with the price list, we calculated an estimation of the profit FinFisher generated through the sale of surveillance products licenses. Applying the retail price to all the licenses available in the database, they amount to a total of €47,550,196, or €98,362,554 if we consider all the licenses marked as “deleted” too. Consider that the FinFly ISP licenses were not taken into account as no price was provided, and that support and training costs were not included in this estimation. Therefore we could realistically expect a higher number.” WikiLeaks
Screenshots of WikiLeaks documents revealing FinFisher’s license agreements:
Shouldn’t there be some sort of control to ensure that developers like FinFisher don’t sell their surveillance products to questionable governments? And why do companies like FinFisher still receive support and protection from countries like Germany and Australia that are so clearly against human rights violations in other, non-digital realms?
As an anti-malware company, we at Emsisoft believe these are important questions to ask.
Note: If you attempt to navigate to wikileaks.org to read the official statement, Emsisoft Web Protection will prevent access by default. This is a safety measure, to prevent accidental download of the malware hosted there. To gain access, simply create a new Web Protection rule granting access to the website – but please, only do so with caution.
Follow up article “A Statement from Emsisoft on WikiLeaks and the FinFisher malware“.
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trialHave a Great (Malware-Free) Day!