The State of Ransomware in Q1 2025

Where we stand
With the first quarter of 2025 in the books, it would be immensely satisfying to report that ransomware attacks have plummeted and that the criminals responsible have largely been brought to justice — not quite. While that would be a pleasant dream, the reality is far less rosy: the cyber threat landscape remains highly active and shouldn’t be taken lightly.
The truth behind the numbers
The dark truth behind ransomware statistics is this: no one knows exactly how many attacks take place — or how many victims there truly are. No one.
The best we can do is piece together a rough idea of the threat’s scope by scouring a variety of imperfect sources: dark web leak sites operated by threat actors, cybercrime forums, and Telegram channels. Each of these has its own challenges:
- Cybercriminals lie. They’re criminals, after all. They may post information about an alleged victim that was the handiwork of another group. They lie to victims. They lie to each other. Why? Hubris? A desire for attention or credibility? Your guess is as good as mine.
- Not all victims are posted. It’s common for an attack to make the local news, only to be claimed on a dark website weeks or months later — often as a pressure tactic during ransom negotiations. And if a ransom is paid quickly? There may be no public claim at all.
- Some groups don’t use dark websites. It’s not uncommon for loose associations of misguided individuals to be identified and arrested by law enforcement with no ties to existing ransomware groups.
- Cybercriminal groups can be relatively nebulous: appearing, morphing, and disappearing regularly. Keeping track of them has been likened to playing whack-a-mole. Cybercrime group Conti, whose internal communications were very publicly leaked in 2022, morphed into BlackBasta (who’s internal communications were leaked in February of this year). These shape-shifting identities are just a fraction of the tangled web documented in the OCD World Watch ransomware ecosystem map.
Tracking the chaos: What the data tells us
Despite all this uncertainty, a few excellent resources help track ransomware-related activity across multiple platforms. These include:
- Ransomlook.io (open source)
- Ransomwatch.telemetry.ltd (open source)
- Ransomware.live (project by Julien Mousqueton)
That their data isn’t identical is part of the story — it reflects just how fragmented this space is. Yet, their Q1 2025 numbers are surprisingly aligned:
- Ransomware.live: 2,251 incidents, 67 active groups
- Ransomlook.io: 2,509 incidents, 76 active groups
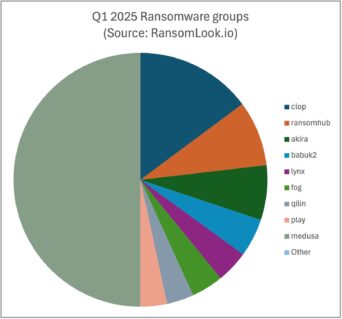
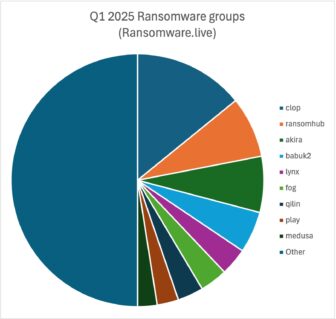
The most active ransomware groups tracked in Q1 2025 were strikingly consistent across platforms, suggesting a core cluster of dominant players:
According to Ransomware.live, victims were recorded in 107 countries in the first quarter of 2025. The top 10 most affected were:
| Country | % of Victims |
|---|---|
| United States | 47.9% |
| Canada | 5.8% |
| Germany | 4.8% |
| United Kingdom | 3.8% |
| India | 2.6% |
| France | 2.6% |
| Brazil | 2.5% |
| Italy | 2.1% |
| Australia | 2.0% |
| Other | 26.1% |
Why the numbers are almost certainly too low
Let’s look at just one major breach to illustrate the scale of underreporting.
The target victim was PowerSchool, a company offering cloud-based software solutions provider for K-12 schools and districts that supports over 60 million students and over 18,000 customers worldwide. They suffered a major breach in late December 2024 that came to light in early January 2025, and data from thousands of their customers — school districts across the US and beyond — was compromised.
This one breach impacted hundreds of school districts and thousands of schools in the US alone. The scope is hard to fathom: the personal data of millions of students going back as far as 30 years or more was stolen. Attribution for the attack has never been established, PowerSchool hasn’t confirmed which districts were affected, and many school districts aren’t particularly forthcoming about data breaches, so those thousands of compromised K12 schools aren’t reflected in any of this data.
Mandatory reporting of cyber incidents including meaningful data would be useful in helping to determine the scope and nature of the threat, and how to best protect against it.
Bottom line? The number of ransomware victims in Q1 2025 was enormous — and significantly underreported.
Ransomware Highlights from Q1 2025
Here are a few major developments that made headlines this quarter:
Chinese threat actors make headlines
Volt Typhoon & Salt Typhoon have been infiltrating US infrastructure and telecoms for years now, but the issue has really come to the fore in 2025. During a secret meeting in Geneva between US and Chinese officials in December 2024, China apparently admitted to US officials that it was behind the Volt Typhoon attacks on US infrastructure. That China was responsible for the attacks wasn’t news. That China alluded to being behind them was astonishing. In March, not long after the meeting, the US DoJ charged 12 Chinese nationals with “numerous and widespread hacking of email accounts, cell phones, servers, and websites.”
North Korea’s billion-dollar heist
In a theft of eye-watering proportions, the DPRK (North Korea) has successfully stolen $1.5 B in cryptocurrency. And everyone knows it.
Law enforcement wins
Lest we leave you with a sense of helplessness in a global game of cyber-intrigue, international law enforcement continues to track, arrest and bring to justice the criminals behind the cybercrime pandemic.
- Dutch and US authorities dismantled a Pakistan-based cybercrime network called Saim Raza or HeartSender
- In January, the FBI and Europol coordinated the seizure of multiple forums widely regarded to harbor cybercriminal activity, including Cracked.io and Nulled.io. Banners posted on the websites read “This website, as well as the information on the customers and victims of the website, has been seized by international law enforcement partners.”
- Individuals associated with cybercriminal groups Phobos & 8Base players arrested and seized 8Base’s dark website. In February, two men and two women, suspected of being European nationals behind Phobos ransomware attacks on multiple Swiss companies between April 2023 and October 2024, were arrested in Thailand
What you can do to protect yourself
There’s no silver bullet, but following best practices can drastically reduce your risk:
- Keep software and device firmware updated — including routers and firewalls.
- Make sure firewall software is installed and enabled on all of your devices.
- Install endpoint protection — or even better, endpoint protection with EDR — on all of your devices to help mitigate malware if it gets past your perimeter defenses.
- Backup your files offline or in the cloud. Encrypt them if possible.
- Use strong, unique passwords for every account. Never reuse them.
- Disable unused services like RDP on all devices.
- Change default usernames and passwords on all equipment.
- Enable MFA (multi-factor authentication) or Passkeys wherever possible.
- Train staff regularly on phishing and other threats.
- Develop and test an incident response plan — make sure everyone knows their role.
In Summary
Ransomware continues to pose a serious global threat — one that evolves constantly and is difficult to quantify. But knowledge, preparation, and collaboration make a real difference.
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free TrialStay informed, stay prepared, and stay safe.