What is Mastodon and is it secure?

As Twitter continues through its late-2022 transformation, a social media network called Mastodon is in the news as a potential alternative. Like Twitter, Mastodon is a micro-blogging website. Mastodon, however, operates very differently from Twitter, and brings with it different security considerations.
Due to the shakeup at Twitter, Mastodon is experiencing surge in interest and explosive growth. In just a few days, Mastodon saw its active user count at least triple, a move that seems to be led by information technology (IT) professionals, such as systems administrators, programmers, and information security practitioners.
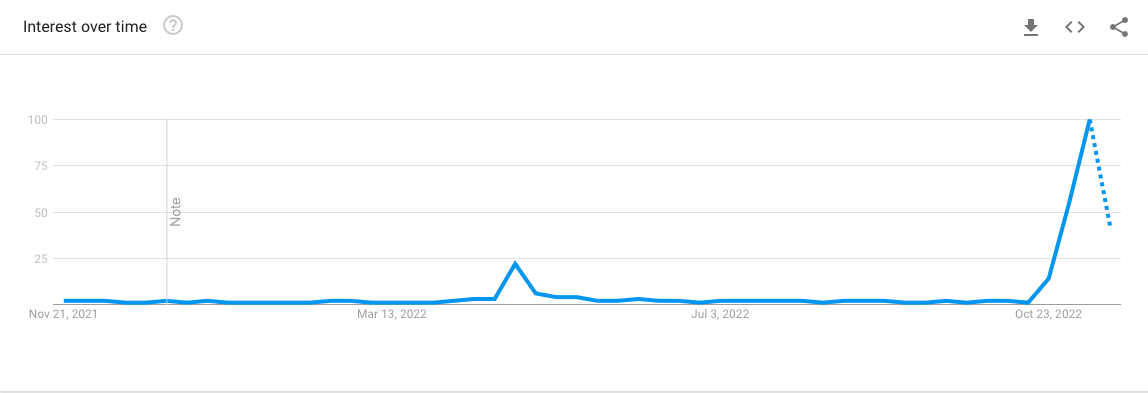
Search interest in Mastodon – Google Trends
Journalists followed, and it is quite possible that Mastodon’s growth is now self-sustaining, meaning that in early 2023 it may well have a large enough user base to be as relevant to organizations of all sizes as more traditional social media networks, such as Facebook, Twitter, Instagram, or TikTok. So how does it work?
What Mastodon is
Unlike traditional, corporation-run social media networks, Mastodon is a decentralized network of servers – or “instances” – largely run by volunteers. Each instance is run by an administrator, and that administrator may decide to federate – which is a fancy way of saying “connect” – the instance with other instances, or not, as they personally choose.
A single, non-federated Mastodon instance functions almost exactly like a traditional centralized social media network. If you want to message someone specific they also need to have an account on that Mastodon instance. You cannot send a Direct Message to someone’s account on another instance. Like Facebook or Twitter, such a Mastodon instance stands alone. Counter.social is an example of a Mastodon instance that has chosen this path, ultimately growing into its own social network with its own culture.
Decentralized-but-federated social media networks like Mastodon, however, are more like email. Anyone can stand up an instance using any domain name they choose. If the instance administrator chooses to federate with the “Fediverse” (the largest network of federated instances), then messages, statuses, likes, follows, and other social media interactions can be exchanged between instances.
The Fediverse is full of similar decentralized platforms, with Mastodon being just one software option out of several. There are options for everything from image and file hosting to podcasting, and even a decentralized pastebin alternative, with most Fediverse applications using the ActivityPub to share messages across the Fediverse.
The Fediverse – and Mastodon along with is – is a very 1990s view of what the internet is and how it should work. Everything is about democratizing access to the services we use every day, preventing any single centralized source from owning our data, or deciding whether or not we can use a given a type of service.
What Mastodon isn’t
Mastodon is emphatically not a Twitter replacement. This is perhaps the greatest source of confusion amongst “bird app refugees” (yes, that is what former Twitter users are called on Mastodon) is that Mastodon clients look very similar to Twitter clients, however, many of the underlying mechanics work differently. These differences have implications not only in how the applications are used, but they also result in different security considerations.
The biggest difference between Mastodon and Twitter is that “the algorithm” doesn’t exist on Mastodon. Traditional centralized social media networks are profit-driven: the more you interact with the application, the more money they make. As a result, there is an algorithm somewhere that surfaces the posts of others based upon your interests. This might seem like a relatively small difference, but its impact cannot be overstated.
Decades of research have shown that feeding news, hashtags, and posts which make people angry get more views, more clicks, and more posts. And since “engagement” drives profit, the easiest way for a profit-driven social media network to make money is to keep them angry, and thus engaged. Mastodon is deliberately designed not to behave like this.
Consider, for example, the basic social media interaction of “favoriting” or “liking” a post. In a traditional social media network this action would “elevate” a post. The more likes it got, the more likely that post would be to be presented to someone by The Algorithm.
On Mastodon, favoriting a post doesn’t elevate it, only the original post author sees that you favorited it, and on most instances the number of favourites aren’t even counted. “Favoriting” simply lets the poster know you liked their post.
If you want to elevate someone’s post on Mastodon you can “boost” it, however, that will only reblog the post to your followers, helping your followers discover great content, but not otherwise elevating the original post or the original poster.
Similar design decisions were made about the Mastodon search capabilities. The primary use for the search box is to find individuals so that you can follow them. You put in their mastodon handle and instance – for example @[email protected] – and this allows you to find and follow accounts located on your instance, as well as on any instance your instance is federated with.
The search box can also be used to search for hashtags, but it cannot be used to search for text inside an individual post. This limits the utility of Mastodon for data mining, while also making it harder for journalists and trolls alike to find specific posts, or any post that doesn’t use a hashtag.
Is Mastodon secure?
All of these differences have an impact on Mastodon’s security. In addition to the differences in the code bases of the applications, the design decisions underlying how these applications were designed in the first place result in different attack surfaces, and a thus present a different risk profile to users.
So what does the security posture of Mastodon look like? The answer is “a lot like the decentralized social media platforms of the 80s and 90s”, with all the same attendant threats, advantages, and considerations. Whereas Facebook and Twitter have a risk profile that resembles a single gigantic online forum grown massively out of control, your mental threat model of Mastodon should be closer to email, Internet Relay Chat (IRC), or, if you’re old enough to remember, interconnected Bulletin Board Systems (BBSes).
All social media has risks
Regardless of which social media platform you use, the biggest risk you are likely to face is account takeover: someone might figure out how to log in to your account, read all your Direct Messages (DMs), and maybe even impersonate you. As a result, security and privacy controls tend to be far more important for mitigating your risk than worrying about any vulnerabilities in the underlying code of the platform.
Enabling two-factor authentication for all of your social media accounts will do more to elevate your security posture than literally anything else you can do. Similarly, taking advantage of advanced posting restrictions (such as the ability to make certain posts “friends only”) can make it harder for malicious individuals to seek you out as a potential target, whilst still allowing you to interact with your friends on that platform.
Impersonation is probably the second biggest threat on social media. Grifters and con artists are constantly looking for any way to get victims to trust them, and the ability to impersonate friends, co-workers, and even celebrities has proven an effective means of attack.
Traditional social media platforms put effort into mitigating this with account verification, such as the old “Blue Tick” system that Twitter used to have, but no such system exists on Mastodon.
All social media platforms are also vulnerable to attacks from client software. In some cases, the only clients you can use to interact with the platform are written and controlled by the company that runs the platform (TikTok is an example), while for other platforms third-party clients exists which can give you a radically different user experience (Twitter and Mastodon are examples here). Software vulnerabilities may exist in social media client software which exposes your data, either to the developer of the client software, or to third parties.
The other major security consideration that all social media platforms share is “who can read your supposedly private DMs”. On all platforms whomever runs the platform ultimately has the ability to do anything they want with your data. Each platform has different controls and rules, but this is a universal vulnerability. Twitter, for example, is rumoured to have at one time had up to half the staff having access to anyone’s DMs. Facebook also has a fairly broad attack surface when it comes to who can read your DMs.
Mastodon security considerations
Decentralized social media platforms such as Mastodon have multiple instances, and each instance has one or more administrators. The administrator of your instance can read any DMs on their instance. If you DM someone across instances, then the administrator of both instances can read those DMs. If this bothers you, you can stand up your own Mastodon instance, giving you complete control over DMs within that instance. This is the same threat model as email, IRC, BBSes, and other decentralized communications.
Additionally, “DMs” on Mastodon aren’t really “DMs” in the same way that they are on other platforms, and should be considered more vulnerable. DMs are really just posts whose visibility is restricted to the people mentioned in the post – which means that if you mention somebody in a post, that particular post becomes visible to them.
Mastodon also tends to have many more clients to choose from than the centralized social media platforms. Each client will have a different set of bugs, and a different set of vulnerabilities. While many social media platforms do have third-party clients, the clients for Mastodon tend to be open source, with little or no commercial backing. This means you can generally alter them if you want, but also that there’s nobody to sue if the client compromises your data.
As an emerging platform developed and administered by volunteers, several privacy risks have been identified with Mastodon, as well as code bugs that contain serious vulnerabilities. Unlike vulnerabilities due to design choices, however, code bugs and even most privacy issues will eventually be sorted as the Mastodon platform matures.
Another difference in the risk posture of Mastodon versus other platforms is stability. Individual Mastodon instances aren’t designed to handle millions of users. The platform is designed to have thousands of instances to distribute the load. Choosing to join smaller instances helps keep the network as a whole more stable, but it can mean that you aren’t as familiar with your instance administrator’s personal track record with regards to privacy as you might be on the more populous instances.
Traditional, centralized social media platforms are designed for massive scale, making them stable even with millions (or billions!) of users. They often employ chaos engineers who attack the system from the inside to ensure that it is resilient against multiple types of failures.
Centralized social media platforms, however, tend to be vulnerable against malicious attacks by the administrator (or CEO), something Mastodon is explicitly designed to be resilient against. If an administrator goes rogue their instance can be “defederated” from the rest of the Mastodon network, constraining the damage they can cause to their own instance.
How to minimize your risk
Since the biggest concern you’ll face on any social media network is account takeover, the best thing you can do to protect your data is to enable 2-factor authentication (2FA) or multi-factor authentication (MFA). In Mastodon, this can be found under Account > Two-factor Auth.
You can also participate in the development of Mastodon, either by directly contributing code, or simply participating in the conversation. For example, at time of writing, there is a lively technical discussion on how to simplify cross-instance following, and the choices made here have the potential to have far-reaching security implications for all users of Fediverse Mastodon instances.
Unlike with centralized social media, anyone and everyone has the opportunity to be part of developing – and securing – Mastodon.
Choosing your instance – and thus the individual(s) that act as administrator – is very important, though this is true of both centralized and decentralized social media platforms. Whether Mastodon or a more traditional social media platform in all cases you need to care a great deal about who is in charge.
Lastly, you can help minimize your risk by following information security professionals on Mastodon to stay up to date with information security news! A significant portion of the Information Security community from Twitter has joined either the Infosec.Exchange or Defcon.social Mastodon instances. Emsisoft can be found on the Fediverse at @[email protected], but we’re not very active yet.
Additional Resources
Want to find a Mastodon instance to join? Instances.social is the tool for that!
Want to find out more information about an instance? The Fediverse Observer can help.
Twitodon can help you find the Mastodon accounts of your Twitter contacts who have also used Twitodon.
Lastly, Fedifinder can help you find the Mastodon accounts of your Twitter contacts who have put their Mastodon accounts in their Twitter bios.
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free Trial