Ransomware Profile: LockBit

LockBit is a strain of ransomware that blocks users from accessing infected systems until the requested ransom payment has been made. It has been highly active since it emerged in September 2019 and has impacted thousands of organizations around the world. Many of LockBit’s attack functions are automated, making it one of the most efficient ransomware variants on the market.
What is LockBit?
LockBit is a ransomware variant that encrypts files using AES encryption and demands a large ransom (typically high five-figures) for their decryption. Whereas most modern strains of ransomware are manually operated, LockBit’s processes are largely automated, which allows the ransomware to propagate and infect other hosts with minimal human oversight after the initial point of compromise.
LockBit operates under the ransomware-as-a-service (Raas) business model, whereby ransomware developers lease their ransomware to affiliates who receive a portion of ransom payments received from the attacks they carry out.
Double extortion, in which threat actors use stolen data to pressure victims into paying the ransom, has become standard procedure among most ransomware groups and LockBit is no exception.
The history of LockBit
LockBit was first observed in September 2019. It was originally known as ABCD ransomware due to the .abcd file extension that older versions of the ransomware would append to encrypted files. In later versions, the file extension was changed to .LockBit.
In May 2020, LockBit began working with Maze in what some referred to as a “ransomware cartel”. It is believed that the two groups shared tactics and resources, with LockBit using Maze’s leak site to publish stolen files. LockBit went on to launch its own leak site in September 2020.
In August 2020, INTERPOL warned of a spike in LockBit attacks on medium-sized companies in the Americas as part of its Cybercrime: Covid-19 Impact report (Note: link starts PDF download).
In June 2021, LockBit launched LockBit 2.0 along with an advertising campaign to recruit new affiliates.
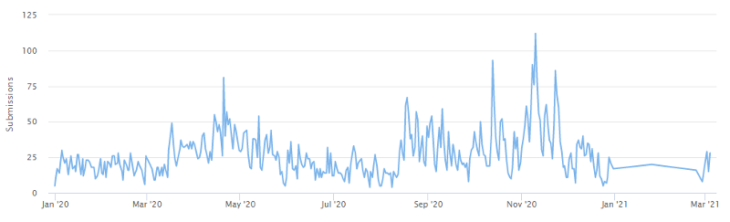
Since LockBit was first discovered, there have been 9,955 submissions to ID Ransomware, an online tool that helps the victims of ransomware identify which ransomware has encrypted their files. We estimate that only 25 percent of victims make a submission to ID Ransomware, which means there may have been a total of 39,976 LockBit incidents since the ransomware’s inception.
LockBit’s affiliate program
As is the case with other RaaS operations, affiliates keep 70 to 80 percent of the proceeds of attacks with the balance being retained by LockBit’s developers.
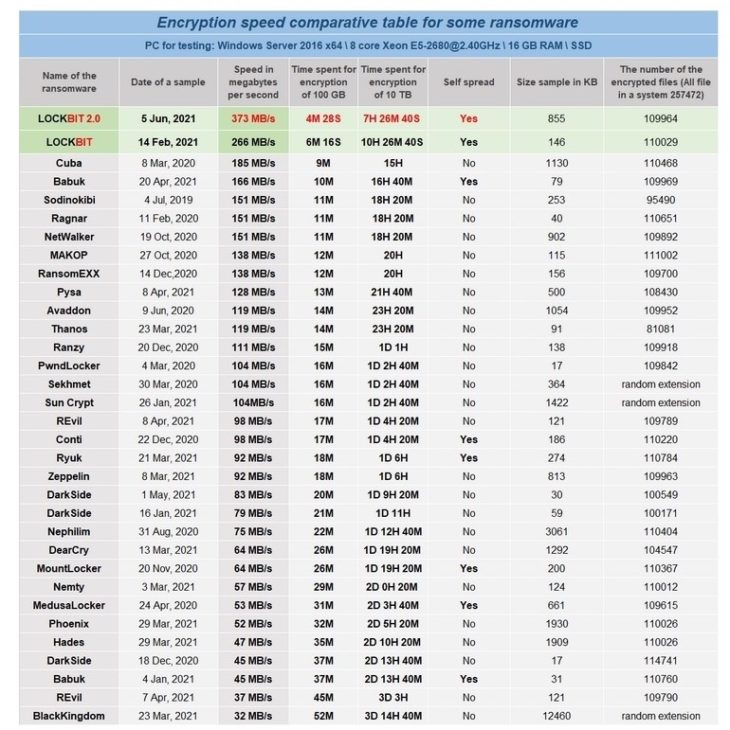
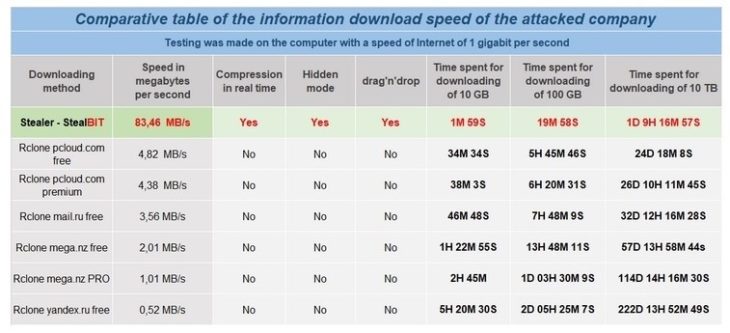
In an attempt to recruit affiliates, the developers have benchmarked LockBit’s encryption performance against multiple other types of ransomware. LockBit also claims to offer the fastest data exfiltration on the market through StealBit, a data theft tool that can allegedly download 100 GB of data from compromised systems in under 20 minutes.
LockBit ransom note
After the encryption process is complete, LockBit drops a ransom note called “Restore-My-Files.txt” in all infected directories and changes the desktop wallpaper on the target system. The note contains instructions on how to make payment and warns the victim to avoid using third-party decryption software and recovery services. The ransom note also contains a link to a payment portal where victims can “Chat with support” and access a one-time free decryption to verify that the attackers have a legitimate copy of the decryption key.
Below is a sample LockBit ransom note:
All your important files are encrypted!
Any attempts to restore your files with the thrid-party software will be fatal for your files!
RESTORE YOU DATA POSIBLE ONLY BUYING private key from us.
There is only one way to get your files back:
1) Through a standard browser(FireFox, Chrome, Edge, Opera)
| 1. Open link [REDACTED]
| 2. Follow the instructions on this page
2) Through a Tor Browser – recommended
| 1. Download Tor browser – hxxps://www.torproject.org/ and install it.
| 2. Open link in TOR browser – [REDACTED]
This link only works in Tor Browser!
| 3. Follow the instructions on this page
### Attention! ###
# [REDACTED] may be blocked. We recommend using a Tor browser to access the site
# Do not rename encrypted files.
# Do not try to decrypt using third party software, it may cause permanent data loss.
# Decryption of your files with the help of third parties may cause increased price(they add their fee to our).
# Tor Browser may be blocked in your country or corporate network. Use hxxps://bridges.torproject.org or use Tor Browser over VPN.
# Tor Browser user manual hxxps://tb-manual.torproject.org/about
Who does LockBit target?
LockBit targets organizations of all sizes, from small businesses to corporate enterprises. Industries most heavily impacted by LockBit include software and services, commercial and professional services, transportation, manufacturing, and consumer services.
Before the encryption process begins, LockBit verifies the location of the compromised system. If the system is determined to reside in the Commonwealth of Independent States, the ransomware automatically aborts. This is likely to avoid gaining the attention of law enforcement authorities in that region.
How does LockBit spread?
As noted earlier, LockBit attacks are largely automated, allowing threat actors to operate with a high level of efficiency and progress from initial access to ransomware execution in a matter of hours. For context, most ransomware groups will spend days or even weeks in the target network before executing the ransom payload.
The LockBit attack chain begins by gaining access to the target network, typically via compromised remote desktop protocol, phishing campaigns, credential stuffing or exploiting known security vulnerabilities. The malware then prepares the target environment by disabling security services, dropping keyloggers, deleting shadow copies and enumerating all accessible directors and network shares. Prior to encryption, high-value data is exfiltrated to hosting services such as MEGA’s cloud storage platform. The stolen data is used as additional leverage to coerce victims into paying the ransom.
Once the exfiltration process is complete, attackers generate a unique LockBit sample from the LockBit management panel, which is accessible to all affiliates. This sample is then manually executed inside the target system, encrypting the victim’s files and delivering the ransom note.
As LockBit operates as a RaaS and can be distributed by many different affiliates, the exact anatomy of an attack can vary from incident to incident.
Major LockBit attacks
- Press Trust of India: In October 2020, the Press Trust of India, the largest news agency in India, was the victim of a LockBit attack. The incident disrupted operations and prevented the company from delivering news to the hundreds of media houses around India that depend on the Press Trust of India for their daily news coverage. No ransom was paid and IT teams were able to restore the affected systems overnight.
- Merseyrail: In April 2021, UK rail network Merseyrail was allegedly hit by LockBit. News of the incident surfaced after threat actors hijacked a director’s Office 365 email account and sent a message to employees and journalists (including BleepingComputer’s Lawrence Abrams, who first broke the story) informing them of the attack and claiming that employee and customer data had been stolen.
How to protect the network from LockBit and other ransomware
The following practices may help organizations reduce the risk of a LockBit incident.
- Cybersecurity awareness training: Because the majority of ransomware spreads through user-initiated actions, organizations should implement training initiatives that focus on teaching end-users the fundamentals of cybersecurity. Ransomware and propagation methods are constantly evolving, so training must be an ongoing process to ensure end-users are across current threats.
- Credential hygiene: Practicing good credential hygiene can help prevent brute force attacks, mitigate the effects of credential theft and reduce the risk of unauthorized network access.
- Multi-factor authentication: MFA provides an extra layer of security that can help prevent unauthorized access to accounts, tools, systems and data repositories. Organizations should consider enabling MFA wherever possible.
- Security patches: Organizations of all sizes should have a robust patch management strategy that ensures security updates on all endpoints, servers, and appliances are applied as soon as possible to minimize the window of opportunity for an attack.
- Backups: Backups are one of the most effective ways of mitigating the effects of a ransomware incident. Many strains of ransomware can spread laterally across the network and encrypt locally stored backups, so organizations should use a mixture of media storage, and store backup copies both on- and off-site. See this guide for more information on creating ransomware-proof backups.
- System hardening: Hardening networks, servers, operating systems and applications is crucial for reducing the attack surface and managing potential security vulnerabilities. Disabling unneeded and potentially exploitable services such as PowerShell, RDP, Windows Script Host, Microsoft Office macros, etc. reduces the risk of initial infection while implementing the principle of least privilege can help prevent lateral movement.
- Block macros: Many ransomware families are delivered via macro-embedded Microsoft Office or PDF documents. Organizations should review their use of macros, consider blocking all macros from the Internet, and only allow vetted and approved macros to execute from trusted locations.
- Email authentication: Organizations can use a variety of email authentication techniques such as Sender Policy Framework, DomainKeys Identified Mail, and Domain-Based Message Authentication, Reporting and Conformance to detect email spoofing and identify suspicious messages.
- Network segregation: Effective network segregation helps contain incidents, prevents the spread of malware and reduces disruption to the wider business.
- Network monitoring: Organizations of all sizes must have systems in place to monitor possible data exfiltration channels and respond immediately to suspicious activity.
- Penetration testing: Penetration testing can be useful for revealing vulnerabilities in IT infrastructure and employees’ susceptibility to ransomware. Results of the test can be used to allocate IT resources and inform future cybersecurity decisions.
- Incident response plan: Organizations should have a comprehensive incident response plan in place that details exactly what to do in the event of infection. A swift response can help prevent malware from spreading, minimize disruption and ensure the incident is remediated as efficiently as possible.
How to remove LockBit and other ransomware
LockBit uses encryption methods that currently make it impossible to decrypt data without paying for an attacker-supplied decryption tool.
Victims of LockBit should be prepared to restore their systems from backups, using processes that should be defined in the organization’s incident response plan. The following actions are recommended:
- Take action to contain the threat.
- Determine the extent of the infection.
- Identify the source of the infection.
- Collect evidence.
- Restore the system from backups.
- Ensure all devices on the network are clean.
- Perform a comprehensive forensic analysis to determine the attack vector, the scope of the incident and the extent of data exfiltration.
Identify and strengthen vulnerabilities to reduce the risk of a repeat incident.
How Emsisoft can help you
The ransom is not the only expense you’ll have to pay should you get hit by ransomware like LockBit. Downtime, legal, credit monitoring, and data recovery (or permanent data loss) are just some of the other associated costs that come with a ransomware attack.
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trial