In modern cybersecurity, where new vulnerabilities and attack vectors are discovered all the time on a constantly shifting threat landscape, a multi-layered defensive strategy is no longer just a luxury, it’s a necessity.
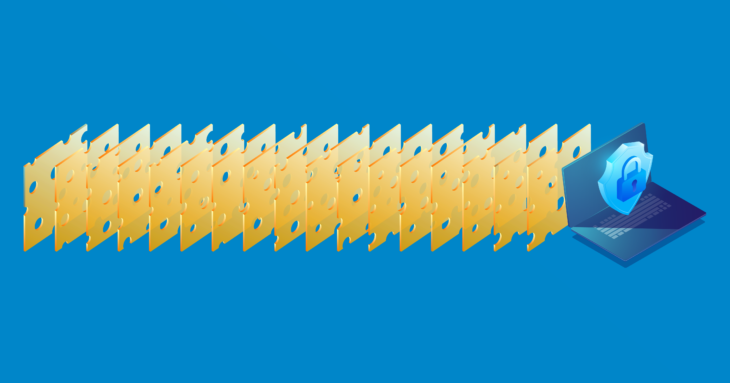
A visual example of this approach is the Swiss cheese model, which portrays the need for having numerous independent layers of protections that overlap to eliminate risks. Unlike a single barrier, with a multilayered approach, in case of failure at one layer, others stand prepared to withstand potential breaches. This adds significant resilience to the cybersecurity landscape.
Understanding the Swiss cheese model
The Swiss cheese model presents a compelling framework, illustrating how multiple layers of security, each with its strengths and weaknesses, work together to create an impenetrable defense system.
The Origins of the Swiss Cheese Model
The Swiss Cheese Model, a concept integral to understanding risk analysis and layered security, was developed in 1990 by Dante Orlandella and James Reason at the University of Manchester. This theoretical model has since been widely adopted across various industries, notably in aviation, engineering, healthcare, and emergency services, to analyze and prevent accidents. It metaphorically represents an organization’s defenses as slices of Swiss cheese, where the holes in each slice symbolize inherent weaknesses or potential points of failure.
The Swiss Cheese Model Explained
Picture a high-security facility, such as a bank vault, designed to safeguard valuable assets. This vault doesn’t rely on a single security measure; instead, it incorporates multiple layers of defense. The first layer might be the physical barrier of the vault door, followed by surveillance cameras, motion detectors, alarm systems, and perhaps biometric access controls. Each of these layers, like slices of Swiss cheese, has its vulnerabilities (holes), but when combined, they compensate for each other’s weaknesses, significantly enhancing overall security.
This is the essence of the Swiss cheese model. It’s about understanding that no single security measure is foolproof when standing alone. However, when layered together, these measures create a formidable barrier against threats, where the weaknesses of one layer are covered by the strengths of another.
Relevance in Cybersecurity
In cybersecurity, this model finds critical relevance. Just like the multi-layered defenses of a bank vault, digital security requires a similar approach. For instance, an antivirus program might stop known threats, but what happens when a zero-day attack occurs? This is where additional layers, like firewalls, intrusion detection systems, and behavior analysis, come into play.
Each layer in a cybersecurity strategy serves a distinct purpose, addressing different types of threats and vulnerabilities. Some layers are designed to prevent attacks, others to detect them, and yet others to respond to and mitigate their impact.
By layering these defenses, organizations can create a cybersecurity system where, even if malware penetrates one layer, subsequent layers secure the protection of critical digital assets. This overlapping, multifaceted approach is essential in a landscape where the nature of threats is as dynamic as the technology they aim to compromise.
How we apply the Swiss cheese model to Emsisoft solutions
By integrating various layers of defense, Emsisoft effectively addresses different aspects and stages of cyber threats, ensuring that vulnerabilities in one layer are counterbalanced by strengths in others.
Slice 1: Web Filtering – Host-based Protection
The first line of defense in Emsisoft’s cybersecurity arsenal is its host-based web filtering. This layer functions like the outer walls of a vault, offering the first barrier to potential threats. Web filtering works by blocking connections to dangerous hosts and is underpinned by an extensive database of malicious hostnames and IPs.
This database is consistently updated, ensuring protection against the latest known threats. The host-based nature of this layer means it is effective across all browsers and most applications, providing a broad shield against a range of cyber hazards, from malware and phishing to potentially unwanted programs.
Slice 2: Browser Extension – URL-based Security
Complementing the host-based web filtering is Emsisoft’s Browser Extension, a URL-based security layer. This acts like the vault’s surveillance system, specifically tailored to the digital environment of your browser. The extension focuses on preventing access to malicious websites known for malware distribution and phishing attacks.
Unlike the broader web filtering, this layer works at a more granular level, filtering harmful content based on URL patterns. It respects user privacy by using hash value matching against local pattern lists, ensuring safe browsing without compromising personal data.
Slice 3: Signature-based Scanning
Signature-based scanning forms a critical part of Emsisoft’s defensive strategy, comparable to a biometric scanner in a high-security system. This layer involves a meticulous analysis of malware samples to identify unique patterns and signatures. These are compiled into a continually updated database, allowing Emsisoft’s software to monitor in real-time and identify threats that match these known signatures.
This scanning is particularly effective against recognized malware variants, acting as a reliable guard against familiar threats. When a match is detected, actions such as quarantine or deletion are promptly initiated, ensuring immediate response to known dangers.
Slice 4: AMSI Scans and Windows Integration
Emsisoft’s integration with Microsoft’s Anti-Malware Scan Interface (AMSI) and IOfficeAntivirus interface is similar to the advanced communication systems within a high-security facility, ensuring seamless coordination between various defense mechanisms.
This slice of protection enhances Windows’ inherent security capabilities by granting Emsisoft’s OnExecution scanner technology access to verify the safety of files and applications. Widely utilized by modern browsers, script interpreters, and Office programs, this integration plays a pivotal role in reinforcing the security of the operating system and third-party applications.
Slice 5: Reputation Lookups (Cloud)
Reputation lookups in Emsisoft’s cloud function like a high-tech access control system, cross-referencing every entity against a vast database of known entities. This database comprises reputation data of over a billion files, providing a comprehensive background check on files encountered by the system. When a file’s reputation is questionable or its detection history is dubious, this layer intervenes, reducing the chances of false positives and enabling a focused response to genuine threats.
Slice 6: Behavior Blocking and System Monitoring
Emsisoft’s Behavior Blocking, the cornerstone of its layered defense, operates much like vigilant surveillance personnel in a high-security facility. This advanced layer, nestled between the operating system and applications, is continuously on the lookout for unusual activities and behavior patterns that might indicate malicious intent. It extends beyond mere static heuristics, encompassing dynamic analysis of system manipulations and potential threats, such as unauthorized code injections or downloaders.
Behavior Blocking is adept at identifying and halting a range of sophisticated threats, including those that attempt to covertly alter the system’s operations. This includes monitoring changes to critical system components like the hosts file and registry.
By responding promptly to these unauthorized alterations, Emsisoft maintains the integrity and security of the operating environment, ensuring that even the most discreet or novel forms of malware are detected and neutralized before they can inflict harm. This proactive approach is key to safeguarding against both known threats and emerging, sophisticated malware types never encountered before.
Additionally, Emsisoft’s solutions are equipped to handle Advanced Persistent Threats (APTs), which are sophisticated, long-term cyber-attacks often aimed at data exfiltration. By leveraging the Behavior Blocker’s capabilities in conjunction with the insights provided by the Remote Desktop Protocol (RDP) monitoring, Emsisoft effectively detects and neutralizes these hidden, prolonged intrusions.
This integration of technologies ensures early detection and intervention, safeguarding against data breaches and prolonged unauthorized access in MSP environments.
Slice 7: Windows RDP Attack Detection
Windows RDP Attack Detection is comparable to a specialized surveillance system monitoring for covert entry attempts. Remote Desktop Protocol (RDP) is a common entry point for cyber attacks. Emsisoft secures this vector by real-time monitoring for multiple failed login attempts, triggering alerts for potential brute force attacks.
This proactive surveillance confirms immediate awareness and response to attempted breaches via RDP, similar to a high-alert security protocol activated upon detection of unauthorized access attempts.
Slice 8: Exploit Protection
Emsisoft’s Exploit Protection functions as a proactive intelligence and defense mechanism in their cybersecurity suite. It plays a critical role in identifying and countering vulnerabilities within applications that could be exploited by cybercriminals to deliver malicious payloads. This layer of security actively prevents applications from executing harmful exploits, including stopping the injection of code into other programs, a common tactic used in cyber attacks.
Application Hardening further fortifies software frequently targeted by cybercriminals. This aspect of exploit protection extends to controlling risky procedures in active programs, such as preventing Microsoft Office and other commonly used applications from executing hazardous PowerShell scripts. By doing so, Emsisoft not only thwarts direct attacks but also strengthens the resilience of these applications, making them less prone to exploitation and enhancing the overall security of the operational environment.
Slice 9: Comprehensive Ransomware Defense
Emsisoft’s approach to ransomware protection is twofold, functioning like a highly specialized response and recovery team within a secure facility. The Anti-Ransomware layer acts preemptively and neutralizes threats before they escalate. It employs behavior monitoring to detect ransomware-specific actions, combined with intelligence networks for early detection of new variants.
Complementing this is the Ransomware Rollback feature, serving as an emergency recovery protocol. When a ransomware attack is detected, the system automatically creates backups of affected files, enabling swift restoration to their original state.
This feature is analogous to having an emergency protocol that quickly restores critical functions and assets after a breach. Together, these layers form a comprehensive defense against one of the most aggressive forms of malware, ensuring both proactive protection and effective recovery in the face of ransomware attacks.
Slice 10: Endpoint Detection and Response (EDR)
Emsisoft’s Endpoint Detection and Response (EDR) functions as a comprehensive command center, continuously monitoring and analyzing detailed telemetry from protected endpoints. This robust system is essential for investigating incidents, providing deep insights into potential threats, and equipping IT teams with the necessary tools for thorough analysis of suspicious files and processes.
The integration of the MITRE ATT&CK framework into Emsisoft’s EDR ensures precise threat analysis and informed decision-making in managing cyber threats. Additionally, Emsisoft’s EDR offers features like osquery-based threat hunting, real-time information collection across devices, and integration capabilities with third-party SIEM platforms, making it an invaluable tool for proactive cybersecurity management.
Slice 11: Emergency Network Lockdown – Device Isolation
Emergency Network Lockdown functions like an emergency protocol in a high-security compound, isolating a threat to prevent it from spreading. Emsisoft allows for the immediate isolation of a single device or a group of devices, effectively containing a threat to stop lateral movement, data exfiltration, or communication with malicious command and control servers. Isolated devices remain connected to the Emsisoft Management Console for investigation, mirroring a secure lockdown scenario where communication lines remain open for coordinated response and control.
Slice 12: Shutdown & Uninstall Prevention
Shutdown & Uninstall Prevention in Emsisoft’s security layers act like a failsafe mechanism within a high-security system, guarding against internal sabotage. This feature prevents unauthorized disabling or reconfiguration of security software, even if an attacker gains full access to a device.
By setting a local security admin password, Emsisoft ensures that crucial security measures cannot be shut down or uninstalled without proper authorization, similar to having a two-key system to prevent unauthorized access to critical controls.
Through Emsisoft’s Management Console, you can configure various user policies. These policies can restrict actions that can be performed with a device using Emsisoft software, providing an additional layer of safeguarding even in the event of a compromise. It’s important to note, however, that while these measures robustly protect Emsisoft’s security environment, devices may still be vulnerable to other forms of tampering if attackers obtain Windows administrative privileges.
Slice 13: Windows Firewall Monitoring & Hardening
Windows Firewall Monitoring & Hardening in Emsisoft’s security approach is akin to having an advanced, tamper-proof perimeter defense in a secure installation. This layer ensures the Windows firewall is active and immune to manipulation by unauthorized users or third-party software.
By continuously monitoring and automatically blocking any attempts to create new firewall rules for specific applications, Emsisoft fortifies the first line of network defense, much like an impenetrable outer barrier that prevents unauthorized entry or manipulation.
Implementing the Swiss cheese model in business environments
Practical Application for Businesses
Regardless of their size and sector, businesses face an array of cyber threats that can compromise sensitive data, disrupt operations, and erode customer trust. Implementing a Swiss cheese model approach means deploying overlapping security measures, like Emsisoft’s layers, to create a robust defense system.
This process involves:
- Assessing Risk: Understanding the specific cybersecurity risks your business faces is the first step in building an effective defense. This includes identifying valuable assets, potential threat vectors, and existing vulnerabilities.
- Layered Security Solutions: Incorporating various security solutions like antivirus programs, firewalls, intrusion detection systems, and employee training. Each layer addresses different aspects of security, collectively enhancing the overall protection.
- Regular Reviews and Updates: The threat landscape is constantly evolving, necessitating regular updates to security protocols and software. Regular audits and updates certify that each layer of defense remains effective against emerging threats.
Customization and Scalability
The beauty of the Swiss cheese model is its adaptability to different business environments. For small businesses, a few well-chosen layers can provide substantial protection without overstretching resources. Larger organizations, on the other hand, can deploy more comprehensive layers, including advanced threat detection and response systems.
Wrap Up
The Swiss cheese model illustrates that no single layer of cybersecurity is impenetrable, but when combined, these layers form a formidable barrier against cyber threats. This layered approach is integral to safeguarding businesses in an increasingly complex landscape.
Business leaders and IT professionals are encouraged to evaluate their current cybersecurity posture and consider implementing a layered protection strategy like that of Emsisoft. It’s about building a resilient defense system that adapts, evolves, and strengthens in the face of ever-changing cyber threats.
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trialPublished March 18, 2021; Updated February 16, 2024.