Spotlight on Ransomware: Common infection methods

Ransomware remains a growing threat with new families cropping up every week. For this reason, we have put together a dedicated series that will focus on the stages of a ransomware attack to offer you protection at every possible level. Being the first post in the series, this post will tackle the first point of contact your system will have with ransomware: infection.
Malware writers and attackers use a variety of sophisticated techniques to spread their malware. There are three commonly used ransomware infection methods that will be explored in this post; malicious email attachments and links, drive-by downloads and Remote Desktop Protocol attacks. It is our hope that we can help you to focus on protecting the areas most likely to be compromised by cybercriminals and to reduce your risk of infection, starting right now.
Here are the most common ransomware infection methods:
Email malware: an oldie but a goodie
This ransomware attack vector can be broken down into two forms:
- Downloading malicious attachments and;
- Clicking on malicious links within emails.
Both require action from you and as such are the most preventable methods of infection.
With malicious email attachments, an attacker creates an email pretending to be from a legitimate company such as FedEx or DPD. A malicious file is attached to the email, in the form of a compressed portable executable (PE) file, a Word document, or a Windows script file. This is where action from the user is needed. The recipient opens the attachment thinking the email has been sent from a trusted source. Once the file is opened or, in the case of a Word document, macros are enabled, the ransomware payload is automatically downloaded and the system infection process starts.
Malicious email links are similar to malicious email attachments, except that the links are URLs embedded in the body of the email. Likewise, these emails are sent from a person or organization that you believe to be legitimate, and when clicked, these URLs download the ransomware.
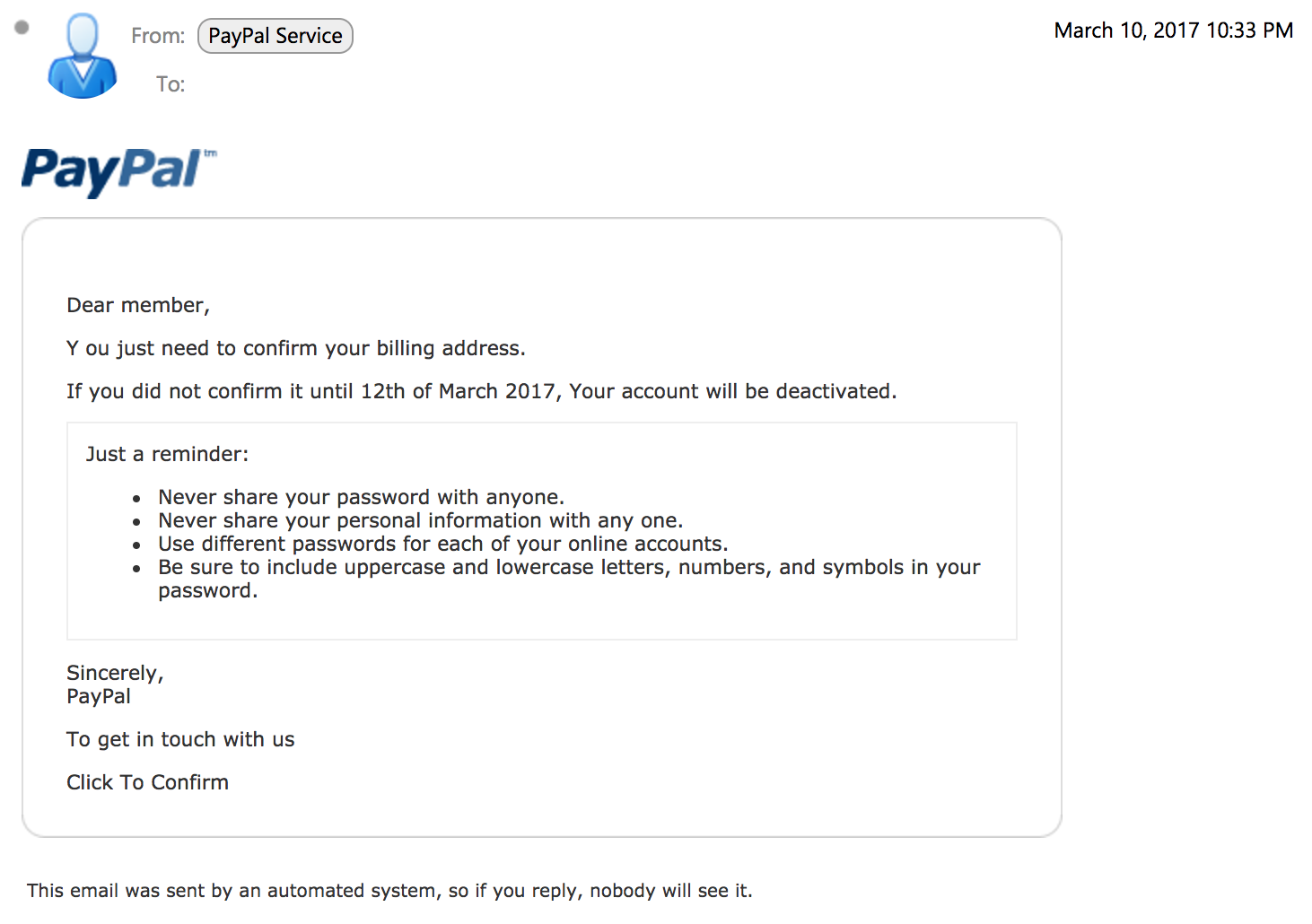
A PayPal email circulating even includes ‘security measures’ to appear more legitimate, however, note the errors in the text such as “Y ou just need to..”
Fake USPS emails that claim your parcel was unable to be delivered offer you a link to print a new parcel label.
Unfortunately, rather than guaranteeing the safe delivery of your parcel, you are instead delivered a malicious payload containing ransomware while looking at the fake shipping label which appears incrediby legit.
The professional appearance of the emails makes them difficult to differentiate from legitimate emails and for this reason they are so effective.
Drive-by downloads: infecting your system without your knowledge
Exploit kits are sophisticated code that exploit vulnerabilities in a system. Most often, they are executed when a victim visits a compromised website, intentionally or not, or by being redirected from a hacked legitimate site to a compromised one. Malicious code is hidden in the page’s code, often in an advertisement (malvertisement), which redirects you to the exploit kit landing page, unnoticed by the victim. This was the case when the New York Times and the BBC were hacked and thousands of readers were redirected to an injecting site.
If there are vulnerabilities in your system, a drive-by download of a malicious payload will be executed and your system held for ransom.
Perhaps the most frustrating thing about exploit kit attacks is the ease with which they access a system without much user action. Because they take advantage of unpatched vulnerabilities in the most popular software, this type of infection can go unnoticed until you are faced with a ransom note with no idea how it got there.
Barrage attacks against RDP servers infect networks rapidly
Remote Desktop Protocol (RDP) attacks, or ‘really dumb password’ attacks, occur when companies leave RDP client ports open to the Internet, and, knowing this, attackers scan blocks of IP addresses for open RDP ports. Once found, hackers will attempt all possible variations rapidly to work out the remote desktop login password which is made easier when a server administrator uses login credentials like username:admin password:admin. Make no mistake, the easiest way to hand access to a hacker is by choosing a weak password. This goes for all users, not only server administrators.
After gaining access to the system, hackers can execute the file that does the encryption and locates all network and local drives. Once a hacker has access to your network, they can do pretty much anything. Recently, three healthcare organizations’ databases were compromised by in this way. A vulnerability in how they implemented their remote desktop protocol (RDP) functionality was exploited, patient files were held for ransom and a further 655,000 were listed for sale on the dark web.
The MongoDB disaster saw 28,200 servers hit. What started as a few isolated incidents transformed into an all out destruction of thousands of MongoDB servers by the end of a week. How were hackers able to gain access to so many servers so quickly? You guessed it. The attacks only targeted those databases left accessible via the Internet and without a password on the administrator account.
Access to a network with 100 computers is a veritable goldmine for hackers. Not only because of the files it has access to, but also the computing power. A botnet can be harnessed to carry out tasks that require a network of computers. A typical botnet may consist of tens of thousands of computers that are all controlled by a single command and control terminal. Hackers love using them because it allows them to combine the computing power and network resources of all the computers in the botnet to attack a single target, send 100,000 emails at once to spread ransomware as rapidly as possible or sniff traffic to capture more usernames and passwords to exploit. Once you have access via RDP, you can do practically anything to the system.
Ransomware prevention requires layered protection
The ease with which ransomware gets into your system is why your best defence is a clear prevention plan. A quality anti-malware suite acts as a solid safety net but with the correct security measures, a rootkit should never get that far.
Here are some practical steps to close the vulnerabilities in your system:
Prevent email and drive-by attacks with common sense
Think before you click. Would FedEx email you an attachment about your shipment or a third party link to a page requesting information? Unlikely, and definitely not as a portable executable (PE) file, a Word document, or a Windows script file. If in doubt, rather than open the email, login directly to the site you are being emailed from and check your account from the safety of the real website.
Prevent RDP attack with the use of complex passwords
Always use complex passwords, especially for Administrator access. Also, consider disabling the Administrator account and using a different name for that access with a less obvious username. Set the system to lock a user out for a period of time after some number of failed login attempts. Additionally, ensure your system has Network Level Authentication configured properly, especially for admin access. On the General tab, select the ‘Allow connections only from computers running Remote Desktop with Network Level Authentication’ check box.
Always run an efficient and powerful anti-malware business solution such as Emsisoft Anti-Malware for Business, Emsisoft Anti-Malware for Server and manage all of your client seats centrally with Emsisoft Enterprise Console.
Prevent malware in all of its forms with regular system cleaning
Backup important files and keep this backup regularly updated
Spring clean regularly with these 5 steps to prevent ransomware infection.
Run a powerful anti-malware suite and keep it updated. Stay protected with Emsisoft Anti-Malware‘s powerful Behavior Blocker with Anti-Ransomware component.
As you can see, there are various methods of infection where ransomware is concerned. Some are preventable through your actions, others require the additional safety net of a quality anti-malware suite. Now that you know the dangers, we hope you will be on the lookout for suspicious emails and strange redirections online. Prevention is the best cure against ransomware, so start preparing.
This is the first post in the Spotlight on Ransomware series. In part two, we dive into what ransomware does once it managed to get onto your system.
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trialHave a nice (ransomware-free) day!