Emsisoft feature highlight: Exclusions for scanning and monitoring


Whitelisting of files and programs via scanner and real-time protection exclusions isn’t anything new really at Emsisoft. But the latest version of Emsisoft’s protection products series enhances the flexibility for power users significantly. A quick showcase of typical use cases for exclusions:
If you open Emsisoft Anti-Malware and navigate to “Settings” -> “Exclusions”, you will see a newly introduced dialog that’s split into two major areas:
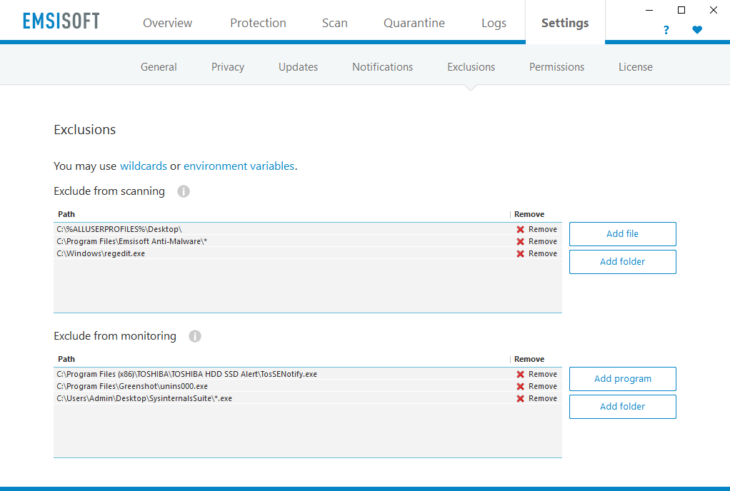
Emsisoft Exclusions Dialog
1. Scanning exclusions
This feature is pretty much self-describing. You select a specific file or a whole folder, and any malware detections during on-demand scans and File Guard scans will be skipped in those places.
Scenario: Remote control software
There are a few remote control tools available that can be legitimately used, but malware authors often bundle them too. If you still need to use these tools, you can exclude their file path from scanning with the Emsisoft scanner.
Scenario: The wanted “unwanted program” (PUP)
Emsisoft’s detection signatures are rather on the more aggressive side when it comes to detection of potentially unwanted programs. At occasions, users may still want to use these programs, like browser toolbars. To avoid detection in future disk scans, simply add their installation folder to the list of exclusions.
2. Monitoring exclusions
Instead of having control over which program files are excluded from scanning, here you can define that actions and behavior of specific programs shouldn’t be monitored.
Scenario: A second antivirus program
Each file reading or writing operation by a program potentially triggers a scan by the File Guard. But scanning a file is also a file operation that may trigger the same thing with a second antivirus program that may be installed. However, if that other antivirus opens a file for reading, it may again trigger another scan with Emsisoft, and so on. The result can be a system lockdown because all resources are used to scan a specific file again and again. To break that loop, you should always exclude any additional real-time protection programs in Emsisoft, and vice versa.
Scenario: Software incompatibility
In order to create world-class protection, Emsisoft’s real-time protection modules need to work closely with the core of the Windows operating system. That technology is called “hooks” and it basically means that our software sits between the operating system and the running programs, to intercept any security relevant operations if needed. Other software also uses hooks to create certain functionality and at times, this creates incompatibilities that lead to crashes or malfunction. If you experience problems like that, you can put the other program on the list of Monitoring Exclusions, to avoid that these programs are touched by Emsisoft’s code.
New feature: Wildcards
Some programs use random filenames, e.g. at installation time, for temporary files. You may not want to exclude the whole temp folder from scanning and monitoring, so you can exclude path patterns like this:
c:windowstempinst*.exe
The * sign replaces a random sequence of characters.
Warning!
While this is a very powerful feature that adds extra flexibility, it is also very dangerous when used wrong. If you accidentally create an exclusion for c:*, you would basically disable the entire protection functionality on your computer, as everything on drive C: would be excluded. Always make sure the wildcard symbol isn’t used at the end of the path sequence, but somewhere in the middle.
If the number of random characters is always expected to be the same, you should better use the ? sign, which replaces just one character. Example if the filename always uses 3 random letters or numbers:
c:windowstempinst???.exe
New: Environment variables
Environment variables are a Windows standard feature that is mostly used by system administrators in command line scripts. They act as placeholders for common paths that may be different on individual installations of the system. Instead of manually looking up the actual path on each computer, you can let Windows do that for you.
Note that environment variables are not just simple placeholders for a static path sequence. Since the protection modules work on System level, environment variables usually match one or many paths on a system. %USERPROFILE% excludes all user profile folders that typically reside at C:Users, not just the profile of the currently logged in user.
Scenario: Excluding a specific installed program
Imagine you are a network admin and manage 10 computers in your office. Some of them still run an old Windows 7 32 bit edition, a few others are on Windows 8 and the newest ones are using Windows 10 in 64 bit editions. You want to exclude a business critical custom software that occasionally triggers behavior blocker alerts. But that program is installed in different places on all of these computers. Some use C:program filesProgramXY, others C:program files (x86)ProgramXY and a few machines have all programs installed on a different drive D:program filesProgramXY. To exclude all these paths in one go without knowing their exact locations, you can simply create an exclusion like this:
%PROGRAMS%ProgramXYMainFile.exe
Scenario: Excluding a file on all user’s Desktops
In corporate environments you will most likely have multiple user accounts used on each computer. Each user has their Desktop files stored in a different user-based folder, e.g. C:UsersMyUserNameDesktop. If you want to exclude all Desktops from all users from scanning, you can simply create one exclusion like this:
%DESKTOP%
This will exclude all matching user-specific folders at once, such as:
C:UsersMyFirstUserDesktop
C:UsersMySecondUserDesktop
C:UsersMyThirdUserDesktop
…
Emsisoft currently supports 44 environment variables
Click on the link “environment variables” in the upper area of the Exclusions dialog to see a tester for all available variables and how they are resolved on your specific system.
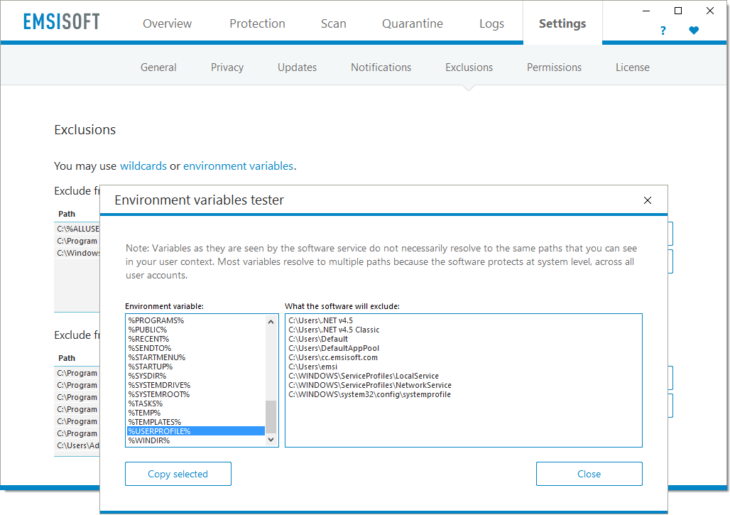
Emsisoft Exclusions: Environment Variables Tester
Available variables (early 2017):
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trial- %ALLUSERSPROFILE%
- %APPDATA%
- %CACHE%
- %CDBURNING%
- %CHROMEPROFILE%
- %COMMONAPPDATA%
- %COMMONDESKTOP%
- %COMMONDOCUMENTS%
- %COMMONDOWNLOADS%
- %COMMONFILESDIR%
- %COMMONMUSIC%
- %COMMONMYPICTURES%
- %COMMONPROGRAMS%
- %COMMONSTARTMENU%
- %COMMONSTARTUP%
- %COMMONTEMPLATES%
- %COOKIES%
- %DESKTOP%
- %DOCUMENTS%
- %DOWNLOADS%
- %FAVORITES%
- %FIREFOXPROFILE%
- %FONTS%
- %LOCALAPPDATA%
- %LOCALAPPDATALOW%
- %MUSIC%
- %MYPICTURES%
- %MYVIDEO%
- %NETHOOD%
- %PERSONAL%
- %PROGRAMFILESDIR%
- %PROGRAMS%
- %PUBLIC%
- %RECENT%
- %SENDTO%
- %STARTMENU%
- %STARTUP%
- %SYSDIR%
- %SYSTEMDRIVE%
- %TASKS%
- %TEMP%
- %TEMPLATES%
- %USERPROFILE%
- %WINDIR%
Conclusion: Use exclusions to avoid certain detections and to sort out incompatibilities
While most home users will probably never have a need to create sophisticated exclusions, the newly added flexibility in the latest version comes very handy for system administrators who maintain larger numbers of computers. Emsisoft Enterprise Console fully supports all types of exclusions which allows expert users to define them centrally for the entire network at one single click.


