How it’s done right: Emsisoft’s Behavior Blocker vs. 20 crypto ransomware families

For most of us the idea of losing all our data sends ice cold shivers down our spines. For thousands of companies as well as home users daily this nightmare becomes reality. The reason? Malicious software accurately referred to as “ransomware” encrypted their files. Today we want to take another look at what most people see as one of the biggest threats today, show how to protect yourself from it, and also give you some insights into how Emsisoft helped victims of ransomware to recover millions of encrypted files over the past year.
What is crypto ransomware anyway?
Ransomware is a type of malware (malicious software), that tries to take your files, business data and personal memories stored on your computer hostage. In general there are two types: Screen lockers and crypto ransomware. The idea behind screen lockers is simple: Prevent the user from using his computer by displaying some kind of password prompt that they can’t get around unless they pay for the correct unlock code. This type of ransomware was wildly popular just a couple of years ago, but is almost extinct nowadays as it has been replaced by its newer and much more devious sibling; the crypto ransomware. Crypto ransomware doesn’t lock you out of your computer. Instead it locks you out from accessing your files and all the precious information and memories stored within them by the use of encryption.
The idea of ransomware isn’t a particularly new one. In fact the first publicly documented case of ransomware, the “AIDS” trojan, can be traced back to the year 1989, when home computing was still in its infancy. The idea of “AIDS” was to encrypt all the file names on your computer. To restore your system back to normal, you would have to pay a ransom of $189. The malware author was quickly identified back then, as the only way to receive money was to have victims wire or mail it to him, leaving behind an easy to trace paper trail. The success and widespread usage of anonymous currencies like Bitcoin however, makes following the money almost impossible, which allows ransomware gangs to often operate in the shadows for years without being caught.
Once a crypto ransomware makes it onto your system, it will look for files that it finds interesting, like for example pictures, videos, save games, databases, documents and music. It will then encrypt these files using some form of cryptography. The type of cryptography used ranges from easy to break self-made algorithms and methods to impossible to break military grade encryption. After all your files have been encrypted, it will usually get rid of backups and shadow copies of your files, so you can’t just restore them. Last but not least it will leave ransom notes behind all over your computer, making you wildly aware of what just happened and outlining how to pay the ransom to get your files back.
How can you protect yourself from ransomware?
The best defense from ransomware is a good set of backups – stored on a disconnected device. Backups are one of these things we all know we should do, but we rarely do until it is too late, even though they not only protect you from ransomware but more mundane threats like hard disk failure or computer theft as well. As mentioned before, a lot of ransomware will target your backups specifically. That is why it is important to store your backups somewhere, where your computer can’t usually touch them. An external disk drive, that is usually detached from your computer or some kind of cloud based file storage or backup system are a good idea. You can also find a backup buddy and store your backups at a friend’s computer and vice versa. No matter what option you choose, make sure you do them regularly, preferably daily, and also make sure you tested the restoration process at least once.
Your next best bet: Emsisoft
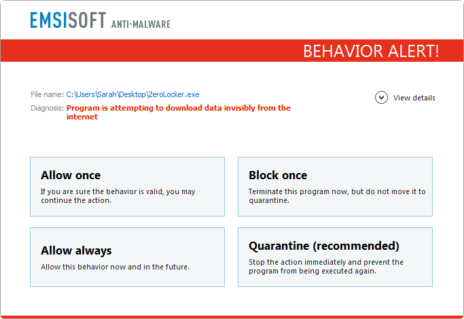
Over the past couple of years, we managed to build a certain reputation when it comes to ransomware. Our malware research team, which is deeply embedded into various major technical support communities like BleepingComputer or Trojaner-Board to monitor new malware trends and outbreaks closely, is quite proud of the fact, that none of the major or minor ransomware outbreaks in the last 5 years affected Emsisoft users in a significant way. To give you an idea of just how effective our products are at keeping even new and yet unknown ransomware from harming your system and the files on it, we thought it would be a good idea to let twenty different ransomware families have a go on a system protected by Emsisoft Anti-Malware.
To make things a bit harder for us, we disabled both the Web Protection, so the malware can communicate with its command and control server freely, as well as the File Guard, so that signature based detection is removed from the equation, as signatures most likely didn’t exist yet at the time the ransomware was first released. We hope you enjoy watching Emsisoft Anti-Malware squash some of the biggest ransomware threats out there, without the help of any signatures, just as much as we do, knowing your system is well protected from all of these and hundreds more.

Click the full screen button to see the details of the alerts
We are here to help
Our commitment to combat ransomware goes far beyond just protecting our users from getting infected by it. In the past couple of years we managed to break dozens of different ransomware variants, helping to decrypt millions of files and allowing tens of thousands of users get back access to their invaluable data. Unlike other companies we provide these services completely free of charge, no matter whether you are an Emsisoft customer or not. So even if your other anti-virus or anti-malware software let you down, we will gladly see if we can help out. Just get in touch with us.
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free Trial