How to use the Behavior Blocker panel to quickly spot potential threats

One of the key protection features of Emsisoft Anti-Malware is the Behavior Blocker, which comes with its own panel that gives you full control over your running programs. If your PC seems to be running slower than usual or behaving erratically, you can use the Behavior Blocker panel to view which programs are running on your system and take action accordingly. Here’s how:
What is the purpose of the Behavior Blocker?
The best way to understand what the Behavior Blocker does is to imagine a layer that sits between your operating system and the programs on your computer. This layer checks for certain malicious behavior patterns in the actions of the programs and raises an alert as soon as something suspicious occurs. For example, if a program is not digitally signed, starts without a visible window, creates an auto-run entry in registry or sends data over the Internet, there’s a good chance it could be a piece of malware.
No matter how encrypted or complex a malware program is, it can’t hide its behavior. Because there are a limited number of ways malware can behave (e.g. a virus will always infect files, a trojan always opens up the system to the outside, encryption ransomware always encrypts files, etc), the Behavior Blocker can detect almost any type of malware, even without requiring frequent online updates.
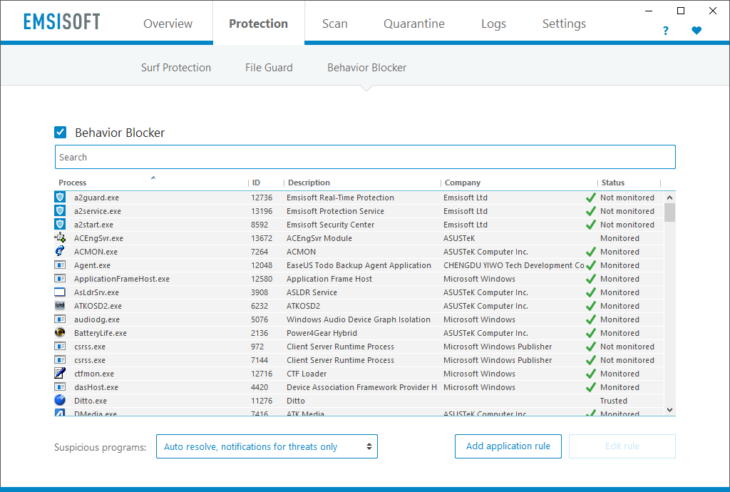
The Emsisoft Behavior Blocker.
However, many legitimate programs behave quite similarly to malware, such as software updaters that may also run in the background and send data over the internet. That’s where the intelligence cloud of the Emsisoft Anti-Malware Network comes in. The Behavior Blocker uses our public malware database to perform a live cloud verification when it notices a program is exhibiting questionable behavior. If the Emsisoft Anti-Malware Network has a clear indication that a program is good or bad, the alert can be skipped and will automatically be allowed or blocked, drastically reducing the amount of false positives. As of early 2018, the Emsisoft Anti-Malware Network knows over 350 million malware threats, and more than 200,000 threats are added daily!
How to change the Behavior Blocker settings
The Behavior Blocker panel has several key settings:
Activate or deactivate the Behavior Blocker
You can activate or reactivate the Behavior Blocker by checking the upper most “Behavior Blocker” option. We don’t recommended disabling the Behavior Blocker as this will significantly lower your overall protection against malware.
Behavior Blocker alert settings
At the bottom of the panel you can configure what Emsisoft Anti-Malware should do with suspicious programs that trigger an alert:
- Alert: If Behavior Blocker detects any suspicious activity, you’ll be presented with a large alert. This alert provides further information you can use to decide whether to keep the program running or shut it down and put it into quarantine.
- Auto-resolve, with lookup notifications: When a suspicious action is detected, Emsisoft Anti-Malware will look the program up online in the Anti-Malware Network database. The progress of this lookup is displayed in a little notification box. Depending on the query result, the program in question is either allowed to continue to run, or shut down and quarantined.
- Auto-resolve, notifications for threats only: The same as the previous option, except it doesn’t display any notifications while a program is being looked up online. You will effectively not see any intrusive boxes for programs that are determined to be safe, but you will see alert notifications when a malicious program is detected and quarantined. This is the recommended default setting.
View details about active running processes
You can view several details about each active running program in the Behavior Blocker panel.
Process and Company columns
The most important columns in the panel to look at are the “Process”/executable filename and “Company” columns. A company name is marked with a green checkmark if the file is digitally signed and the certificate is valid. This is important because any file property information can potentially be faked by malware authors. For example, if you don’t see a checkmark next to a program created by “Microsoft Corporation”, it is not guaranteed that the file is actually from Microsoft.
Status column
The “Status” column provides information about whether a program is currently monitored by the Behavior Blocker or not. Note that certain system processes, Emsisoft Anti-Malware’s own processes and processes that explicitly prevent monitoring will show as “Not monitored”. The same goes for processes that are excluded via the “Exclusions” panel.
Adding or changing an application rule
By double clicking on any one of the running processes, you can change its monitoring state from the default “Monitored” to either:
- Trusted: Always allow the program to run, no matter if it’s flagged suspicious or not.
- Blocked: Prevents the program from starting again in the future.
Choosing a non-default monitoring state option automatically saves a new rule. These rules are displayed in the list of programs even if those programs are currently not active.
Application rules are always bound to a specific version of a configured program. If a program changes (e.g. by performing an update), the application rule needs to be updated, too. By default, Emsisoft Anti-Malware asks you to confirm such updates for safety reasons (a program could have been manipulated by an attacker) but if you would like to avoid those alerts, just check the option “Don’t alert when this file changes” in the application rules settings.
Context menu options to handle programs and find threats
You can right-click on a program to perform several actions: Edit rule, Lookup online, Quarantine process, End process, Open file location, and view File properties.
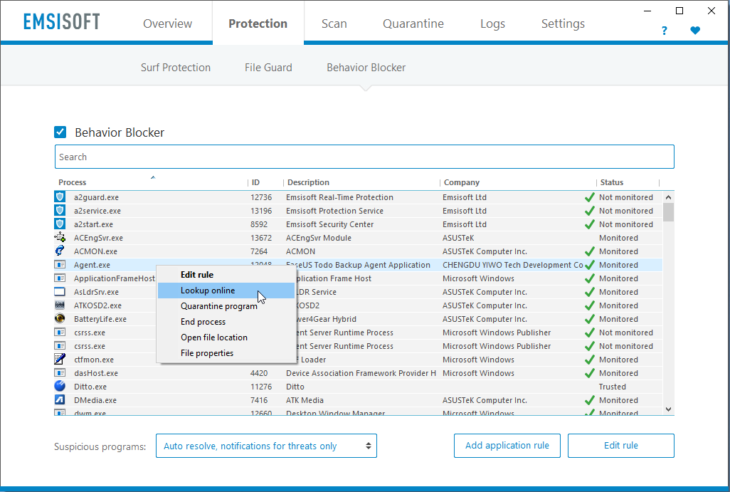
Right-click on any process to perform various tasks to find out more about it.
The “Quarantine” and “End process” options are only available for monitored processes in order to prevent you from harming your system by mistakenly performing one of these actions on a harmless or critical Windows process. Each action will allow you to learn specific details about the program:
Edit rule
Opens the same application rule window as double clicking on a process, as described earlier.
Lookup online
Use this feature to check a file in the Emsisoft Anti-Malware Network. After selecting the desired process, you’ll be directed to a page showing several file properties and details about the executable process that you can use to make an informed decision about the safety of a file.
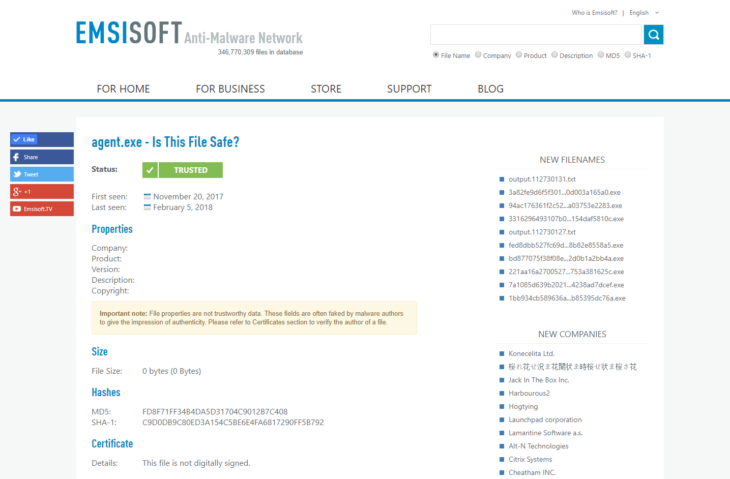
The process list “lookup online” feature using the Emsisoft Anti-Malware Network.
Quarantine program
You can use the “Quarantine program” option to move an unknown or malicious process or program safely to Emsisoft’s quarantine. Once you move a program or process to quarantine it can no longer be accessed or run because it is placed in an encrypted container that will keep it locked. In the event that you mistakenly quarantine a harmless file, you can restore the file from the quarantine at at any given time.
End process
You can use the “End process” option to end an unknown or active malicious process. This means that the the threat cannot harm your PC anymore since it is no longer running. The end process option may be a safer alternative than the quarantine option in the event you are unsure if a process is malicious, but still do not trust it or notice that it is potentially exhibiting suspicious behavior.
Open the file location
Navigate to a file’s location to get insight into where exactly a file is located. For example, if a supposed system process is typically located in the System32 directory but is now present in your Documents folder, it is most likely malware. Experienced users may wish to manually remove threats using this option.
File properties
File properties are traits of the file such as the size or type. Viewing file properties is helpful in determining whether a file is malicious because users can view the MD5 hash of any given file, which can be compared to the authentic hash that can quickly be found online. The MD5 hash of a file is a sequence of 32 characters, which helps identify each file uniquely and comes in handy when you need to check if a file has been manipulated or changed. If the hash is different, there is a high probability that the file is malicious. The date a file was first and last seen is also a factor to take into consideration because if a file is relatively new and not yet classified, it should (in theory) not be trusted.
What to do when you find a malicious process
If a process is found to be malicious, it will most likely be blocked in real time by the Emsisoft Behavior Blocker. Alternatively, use the process list to quarantine or end the active malicious program. If a program is classified as malicious by the Anti-Malware Network lookup, it is recommended that you quarantine the threat.
If the program is unknown, ending the process may be a safer option at the time as the program could potentially be harmless. At this point, running a scan with your security product may be a wise choice to ensure that your PC is free of other potential malware infections. Otherwise, feel free to consult with our malware removal experts on our support forum if you are unsure of which action to take.
Conclusion
The Behavior Blocker panel offers new ways to spot potential threats. You can use the process list to weed out suspected threats and learn several details about which programs are running on your PC. When a malicious process is found, simply use the “End process” or “Quarantine program” option to remove the threat from memory. In addition, you can create application rules to control the manner in which the Behavior Blocker handles certain applications and activities. Use the Behavior Blocker panel to your advantage to get the most out of your Emsisoft protection.
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trialHave a great (malware-free) day!


