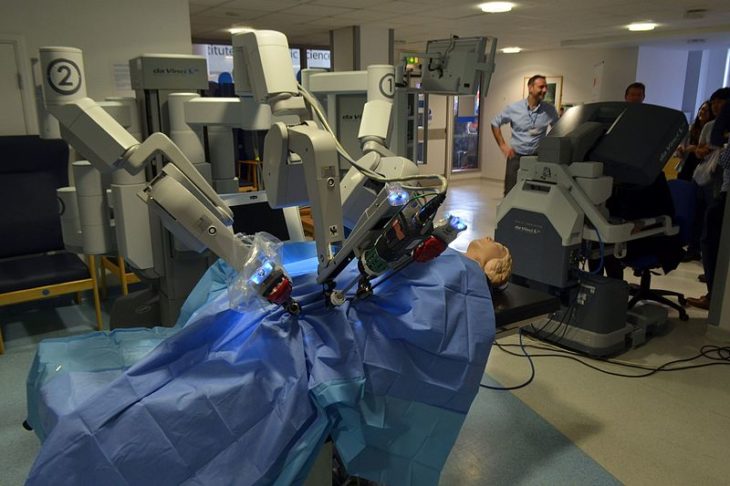
With advances in technology, telesurgical procedures are not uncommon and date as far back as 2001. Researchers at the University of Washington in Seattle examined a product of their own University known as the Raven II and found that it is vulnerable to cyber threats. It was discovered that the robotic could be forced to ignore or override a surgeons commands among other unwanted actions.
According to the information composed in a paper by the researchers, it is also possible for a hacker to initiate a man-in-the-middle attack on the connecting router that will intercept data traffic between the surgeon and robot which means the attacker can remove, modify, or insert commands.
Hackers could potentially hold your life in their hands
According to MIT Tech, the researchers tried out three types of attacks on the robotics.
The first attack changes the commands sent by the operator to the robot by deleting, delaying, or reordering them which causes the robot’s movement to become jerky and difficult to control.
The second attack modifies the intention of signals from the operator to the robot by changing the distance an arm should move or the degree it should rotate. Researchers Bonaci and Co. stated that:
“Most of these attacks had a noticeable impact on the Raven immediately upon launch”
The final category of attack is a complete hijacking that takes over the robot. Bonaci and Co. also stated:
“We effectively took control over the teleoperated procedure”
In an additional test, researchers worked out how to generate movements that triggered the automatic stop mechanism within the robot that resulted in a successful denial of service attack. Afterwards, they easily stopped the robot from being properly reset thus making a surgical procedure impossible.
Encryption can be a life saver but still is not foolproof
It has been determined that the best way to prevent and combat a man-in-the-middle attack is to use encryption to secure the communications between the control console and the robot. As we all know, even with the best, strongest security systems and practices in place, there is always a possibility that a hacker can find a way around the defenses.
Under the circumstances, would you trust a remote robotic operation?
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free TrialHave a safe robotic (hack-free) day!